12th May 2017 was the day when the world saw one of the massive cyber attack in recent times where more that 230,000 computers in over 150 countries were infected by the new type of malware which encrypted the files on the computer system and demanded the ransom in return to the key to decrypt the files. World came to know about the new type of the malware called ransomware after this worldwide cyber havoc. Now even a non tech savvy person became aware of this new cyber epidemic. But rasomware themselves are not new and the first known ransomware attack dated back in 1989 when AIDS trojan hid all the directories and encrypted the files on C drive and making the system unusable. Ransomware attacks in 2016 like the attack on Hollywood Presbyterian Medical Center and San Francisco Municipal Transport Agency was hardly noticed by common mass. The year saw many ransomware variants like Locky, teslacrypt and cryptlocker but didn't caused as much hue and cry as wannacry did.
Understating Ransomware
Since wannacry is a ransomware, the underline working is same as other ransomware variants like Locky or Teslacrypt. It uses the combination of symmetric key and asymmetric key cryptography to make the process faster and more efficient. Ransomware uses symmetric key cryptography to encrypt and decrypt the files because encryption and decryption process using symmetric key is much faster when compared to asymmetric key. To take the control of the symmetric keys and demand for ransom, asymmetric key cryptography is used. Ransomware servers which are hidden in the dark web holds the master key for the decryption of all the files. Ransomware demands for the extortion in the form of crypto currencies like bitcoins in exchange of the decryption keys.
Why Wannacry caused mayhem
Wannacry is not just a malware but it is also a worm i.e it has the self replicating ability and infect other computers on the network without human intervention. Wannacry enters the network in the ways similar to other ransomwares like via attachments in emails or malicious downloads. But once it enters the network, unlike other rasomware it probes for other systems in the network for vulnerabilities to spread. Thanks to the EternalBlue exploit developed by NSA, the wannacry spread to the other systems by exploiting the code execution vulnerability in the Server Message Block (SMB) protocol. This vulnerability helped the execution of ransomware code on the target system without the end user interaction. Since the windows OS user base in gigantic, the number of unpatched windows running all around the globe was also significant. This lethal combination of windows code execution vulnerability and self replicating nature of ransomware made wannycry stand apart from its other siblings.
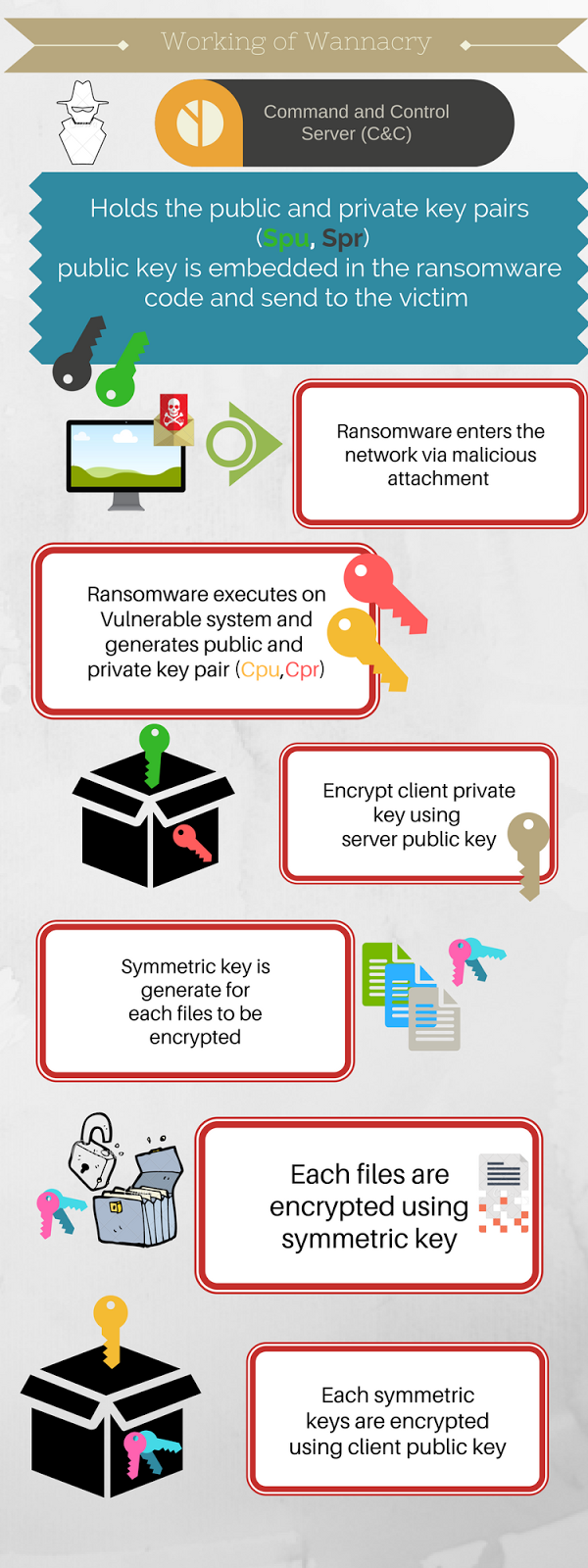
Attack flow of Wannacry
- Ransomware enters the network via spam email. An ignorant user or malicious insider opens the malicious email attachment.
- Infects the system and uses it as pivot to search the other system in the network for unpatched windows machine running with vulnerable SMB protocol.
- Uses the Eternalblue to exploit the vulnerability and spread to other systems.
- Executes the ransomeware to encrypt the files on the system.
Below info-graphic explains the complete flow of wannacry (or in general any ransomware)
Is it possible to get the files back without paying ransom?
Only way to get back time files without paying the ransom is to track down the command and control server and get hold of the key or ransomware author voluntarily giving the server private key as it happened in case of teslacrypt. This will help to decrypt the client private key which was encrypted with server public key. The decrypted client private key helps in turn to decrypt the symmetric keys which were used to encrypted the files using client public key. I know its bit tricky, but try to read it again and again and view the info-graphic above, stuffs will get clear. Please note that in asymmetric key cryptography, encryption is always done using public key and decryption is done using private key.
Another theoretical possibility to decrypt the files are by obtaining client private key. The public and private key pairs are generated on the victim's machine and at some point of time the keys exists in its main memory. The possibility of the obtaining the keys from the memory depends on several factors like the cryptographic library used in the ransomware, keys not being replaced by other processes and so on. Similar decryption tool with limited capability was released for wannacry which obtained the client's private key from the process memory.
Another theoretical possibility to decrypt the files are by obtaining client private key. The public and private key pairs are generated on the victim's machine and at some point of time the keys exists in its main memory. The possibility of the obtaining the keys from the memory depends on several factors like the cryptographic library used in the ransomware, keys not being replaced by other processes and so on. Similar decryption tool with limited capability was released for wannacry which obtained the client's private key from the process memory.
Lesson to learn
Computers connected to the internet remain the soft target of zero day vulnerabilities and the security researchers will always be on their toes to thwart such attacks.
Wise men lay up knowledge but the mouth of the foolish is near destruction
The best thing one can do is to use genuine software/OS and keep their systems updated. Be wise and not act as a fool. Stop using pirated/cracked software because next wannacry may be not too far.
Hope this post was informational. Do comment your suggestions about the post. I will be happy to receive the feedback. Also share if you find it useful.
Follow me on twitter @PiyushSaurabh07 to get updates regarding my future posts.
Happy Learning :)


Well written Piyush, Way to go !!!
ReplyDeleteWaiting for your next post.
Thanks Rahul. 😊Next post will come soon
DeleteThanks Piyush for such a great piece of information 👍
ReplyDelete